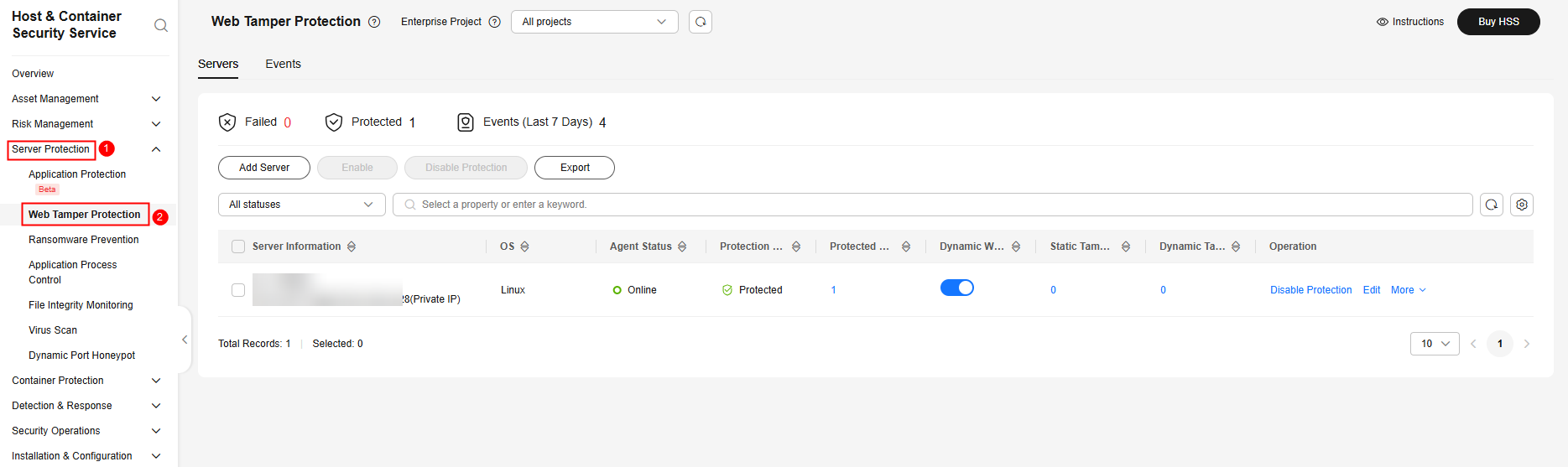
Enabling Protection
To enable protection, allocate a quota to a server or a container. After protection is disabled or the protected server or container is removed, the quota can be allocated to another server or container.
Prerequisites
- HSS can be billed in yearly/monthly or pay-per-use mode. To use yearly/monthly billing, ensure you have purchased sufficient protection quotas. For details, see Purchasing an HSS Quota. If you use the pay-per-use billing mode, you do not need to purchase quotas in advance.
- Ensure that the agent has been installed on the server or container node and is online. For details, see Installing the Agent on Huawei Cloud Servers and Installing the Agent on Third-party Servers.
Constraints
- Server
Before you enable protection for a Windows server, enable the Windows firewall to block the source IP addresses of brute-force attacks. If the Windows firewall is not enabled, HSS only generates alarms for detected brute-force attacks, but does not block them.
- After the Windows firewall is enabled, every time HSS detects a brute-force attack, it adds an inbound rule to the firewall to block the attack source IP address. There are no other impacts on services.
- Do not disable the Windows firewall when using HSS, or HSS cannot block the source IP addresses of brute-force attacks. Once it is disabled, HSS may fail to block the attack source IP addresses even after you manually enable it again.
- Container
HSS can only protect Docker, Containerd, CRI-O, Podman, and iSulad containers.
Enabling Protection
Perform the following operations to enable protection based on the edition you need.
Viewing Scan Details
After server protection is enabled, HSS will immediately perform a comprehensive scan on the server. It may take a long time. After the scan is complete, you can check its details.
- Choose . Locate the server on the Servers tab page.
- Check the Risk Level column of the server.
Table 3 Risk status Status
Description
Pending risk detection
The server is neither protected nor scanned.
Safe
No risks were found in the comprehensive scan on the server; or the protection has just been enabled, and no risks have been found yet.
Risky
The server has security risks.
- Hover the cursor over the risk status to view the risk distribution.
You can click a value to go to the details page.
Follow-up Procedure
HSS provides server and container defense functions for you to enable as needed. For more information, see Manual configurations.
|
Category |
Function |
Reference |
|---|---|---|
|
Security Configurations |
|
|
|
Server Protection |
|
|
|
Container Protection |
|
|
|
Policy Management |
Policy management includes asset management, baseline inspection, intrusion detection, and self-protection policies. Intrusion detection is disabled by default. You can enable and modify them as needed. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot